1. Choose ONE of the four ways to manage and develop integrated systems as listed below;
XML and Web Services as the glue
2. Summarise your understanding and describe its relevance (250 words max) in either your study at university or in your work environment;
XML web services are developed to integrate various systems or to create new applications from existing ones. New powerful applications can be created quite quickly and in a cost effective way when existing applications are exposed as web services.
A web service is one that exposes useful functionality of an application to web users. In most cases, SOAP is used as the protocol. The service provides its description via Web Services Description Language (WSDL) document and is usually registered with Universal Discovery Description Integration (UDDI) so that other users can easily find it.
One of the benefits of web services architecture is that it communicate with different applications written in different languages in a standards-based way. This is extremely helpful when new applications are being created by integrating existing ones since data can be retrieved from all the applications even when they might be written in different languages, hosted in different operating systems using different databases.
Another benefit of using a web service is that they can be used over the standard set of protocols – XML, HTTP, TCP/IP. Therefore, the cost of entry for web services is much lower compare to other technologies.
At work, we created a RSS feed service that was listing the latest updates from three different products (cases, legislation and unreported judgments). We developed this using web services that was calling the various products to get the updates and then created the xml file for the rss.
References:
http://msdn.microsoft.com/en-us/library/ms996507.aspx
3. Edit TWO similar versions (include bibliography) of that summary to CSU Interact:
a. Post version A as a wiki contribution;
b. Add version B as a final entry to close your developer’s blog.
Web services has changed the way applications are created these days and pushing companies more towards web based applications and less on desktop based applications. Web applications can be accessed from anywhere and does not need to be installed making it a better option compared to desktop applications.
Web applications development is also changing and more applications are getting created using web services. Web services, being standards-based, can be used in creating in any applications, making it more reusable. Web services can also be written in various languages and can communicate with other applications in a standards-based way making it much more powerful and portable.
In short, web services is the soul of internet-based services.
References:http://msdn.microsoft.com/en-us/library/ms996507.aspx
Showing posts with label exercise. Show all posts
Showing posts with label exercise. Show all posts
Thursday, May 27, 2010
Tuesday, May 25, 2010
Exercise 15 - Topic 10
1)What is meant by a location based service? Explain using the Web applications found on a late model mobile device.
A location based service (LBS) is one that is accessible via mobile devices and takes advantages of the user's location to provide services to the users. An example would be to find the nearest train station or a bank's branch through the mobile device. Another example would be advertising directly to users depending on the user's location or to provide weather report to the user based on the location.
2)Describe the purpose of the Open Mobile Alliance Initiative.
The Open Mobile Alliance (OMA) is the body that develops open standards for the mobile phone industry. It's mission is to provide interoperable services across countries, operators and mobile terminals. The specifications from OMA are meant to work with any cellular network technology.
3)What are the main components of a mobile Web services framework?
Mobile Web Services framework or Mobile Service Oriented Architecture uses existing emerging standards and extends SOA to mobile devices.
Location Services: Finds information about the user locations and provides him information based on the location.
Voice Services: Call Controls and Rounting.
Data Services: Provides data to user using sms, email, mms.
Identity Services: Checks for the identity of the user.
3rd party Web Services: Web Services created by third party performing various services.
Billing and Payment Services: Provides security while making payment over the mobile device.
4)Visit an airline Web site and search for information on WAP or SMS or 3G mobile application access to booking airline services. The same services exist in banking. How do both industries compare?
Virgin Blue provides Virgin Blue Travel Application that can be installed in a Blackberry from AppWorld. The application provides options to check-in, check boarding passes, create and manage bookings, check airport guide, and provides different information like Velocity Rewards points program. While creating a booking, the app provides option to search for flights and make bookings.
Commonwealth bank does not provide any app on Blackberry, however, the site can be accessed via the Blackberry browser from http://netbank.com.au/mobile. It seemed slow compared to the Virgin Blue app. It had options to view accounts, transfer money and BPay.
Both industries provide different services but security, accuracy and realtime data are the most important concerns for both the industries since both the industries will need to process payments and charge correct fees when applicable.
References:
http://en.wikipedia.org/wiki/Location-based_service
http://en.wikipedia.org/wiki/Open_Mobile_Alliance
http://developers.sun.com/learning/javaoneonline/2008/pdf/TS-5147.pdf
Monday, May 24, 2010
Exercise 14 - Topic 10
1) What is a spider? What does it do?
A spider, also known as crawler, robot, traverses the World Wide Web in an orderly manner. Search engines line Google uses this technology to provide up-to-date search results. The spider downloads the pages from the web, keeps a copy of the pages that is later indexed to provide quicker search.
Spiders can also perform automated maintenance tasks like link validating. It can also retrieve specific information from web pages, like the email addresses.
Using some search engine technology like the FAST search engine, we can specify the web sites to crawl. This allows for creating custom search engines that filters results by the particular web sites, typically a certain type of websites (for example, all Australian news websites).
2) Differentiate the various types of software agents:
The following are the different types of software agents:
a) Collaborative Agents: Collaborative Agents can act rationally and autonomously in open and time-constrained multi-agent environments.
b) Interface Agents: Interface agents support and provide assistance, typically to a user learning to use a particular software. The agent tracks the user using the software and suggests better ways to perform the task as needed.
c) Mobile Agents: Mobile agents are software processes capable of roaming the WWW, interacting with foreign hosts, gathering information on behalf of its owner and retrieve data and complete tasks set by the user.
d) Information/Internet Agents: Information agents have come about because of the sheer demand for tools to help us manage the explosive growth of information and it can traverse the WWW.
e) Reactive Software Agents: Reactive agents is a special category of agents which do not possess internal, symbolic models of their environments. Instead they respond in a stimulus-response manner depending on the state of the system where they are embedded.
f) Hybrid Agents: Hybrid Agents are created based to combat the disadvantages of the five other software agents.
g) Heterogeneous Agent Systems: Heterogeneous agent systems refers to an integrated set-up of at least two or more agents which belong to two or more different agent classes. A heterogeneous agent system may also contain one or more hybrid agents.
http://agents.umbc.edu/introduction/ao/5.shtml
3) Identify various activities in e-commerce where software agents are currently in use:
Examples include:
A spider, also known as crawler, robot, traverses the World Wide Web in an orderly manner. Search engines line Google uses this technology to provide up-to-date search results. The spider downloads the pages from the web, keeps a copy of the pages that is later indexed to provide quicker search.
Spiders can also perform automated maintenance tasks like link validating. It can also retrieve specific information from web pages, like the email addresses.
Using some search engine technology like the FAST search engine, we can specify the web sites to crawl. This allows for creating custom search engines that filters results by the particular web sites, typically a certain type of websites (for example, all Australian news websites).
2) Differentiate the various types of software agents:
The following are the different types of software agents:
a) Collaborative Agents: Collaborative Agents can act rationally and autonomously in open and time-constrained multi-agent environments.
b) Interface Agents: Interface agents support and provide assistance, typically to a user learning to use a particular software. The agent tracks the user using the software and suggests better ways to perform the task as needed.
c) Mobile Agents: Mobile agents are software processes capable of roaming the WWW, interacting with foreign hosts, gathering information on behalf of its owner and retrieve data and complete tasks set by the user.
d) Information/Internet Agents: Information agents have come about because of the sheer demand for tools to help us manage the explosive growth of information and it can traverse the WWW.
e) Reactive Software Agents: Reactive agents is a special category of agents which do not possess internal, symbolic models of their environments. Instead they respond in a stimulus-response manner depending on the state of the system where they are embedded.
f) Hybrid Agents: Hybrid Agents are created based to combat the disadvantages of the five other software agents.
g) Heterogeneous Agent Systems: Heterogeneous agent systems refers to an integrated set-up of at least two or more agents which belong to two or more different agent classes. A heterogeneous agent system may also contain one or more hybrid agents.
http://agents.umbc.edu/introduction/ao/5.shtml
3) Identify various activities in e-commerce where software agents are currently in use:
Examples include:
- News sites that collect news from various websites and displays it as one.
- Credit card comparison sites that compares various credit cards and give results with best rates, personal loans, etc.
Saturday, April 3, 2010
Exercise 13 - Topic 10
Develop the class diagram for the following shopping cart specifications:
A shoppingCart object is associated with only one creditCard and customer and to items in itemToBuy object. Persistent customer information such as name, billing address, delivery address, email address and credit rating is stored in the customer object. The credit card object is associated with a frequentShopper discount object, if the credit rating for the customer is good. The customer can make or cancel orders as well as add and delete items to the shopping cart product. The credit card object contains the secure method for checking that the charge is authentic.
A shoppingCart object is associated with only one creditCard and customer and to items in itemToBuy object. Persistent customer information such as name, billing address, delivery address, email address and credit rating is stored in the customer object. The credit card object is associated with a frequentShopper discount object, if the credit rating for the customer is good. The customer can make or cancel orders as well as add and delete items to the shopping cart product. The credit card object contains the secure method for checking that the charge is authentic.

Exercise 12 - Topic 9
Examine the Use Case in figure 9.2, page 60, and explain the MVC architecture of the online bookstore (the Model, the View and Controllers) needed to Lookup Books and Add to Shopping Cart.
Lookup books:
Lookup books:
- View: A customer looks up or searches for book from a web page.
- Controller: The controller takes in the request, makes a call to the database and loads the data into memory which is the model.
- Model: The model is the object in memory that holds the data that is returned in step 2.
- Controller: The controller retrieves the data from the model and pass it to the view.
- View: The page is displayed that contains data returned in step 4.
- View: A customer add a book to the shopping cart.
- Controller: The controller takes the request, creates the model object and the request to the model.
- Model: The model is the object in memory that contains the book add to shopping cart in step 1.
- Controller: The controller gets the message from step 2 on whether the book has been successfully added or not.
- View: The controller passes the message from step 4 to customer that the book is successfully added or could not be added.
Exercise 11 - Topic 8
1. Give a description in your own words of the ACID properties of a transaction.
ACID (atomicity, consistency, isolation, durability) is a set of properties that guarantee that database transactions are processed reliably. This really refers to what can be described of a single logical operation called transaction. For example, in a sql server database, I may choose to update a customer records in two tables. Usually, I would update the record in one table first followed by the next table. But it may result in such that only one table is updated due to some errors. Using transaction, it would mean that either both the table is updated or none is updated. Once the transaction is completed, the database will be in a consistent state and the changes made by the transaction is permanently stored in the database.
2. Describe a TP monitor environment. How can a TP monitor stop an operating system being overwhelmed?
A TP monitor is a control program that manages the transfer of data between multiple local and remote terminals and the application programs that serve them. It provides integrity by making sure that transactions do not get lost. It has the ability to update multiple different databases in a single transaction and has the ability to attach priority to transactions and provide security.
With the TP monitor technology, a client connects to the TP monitor instead of the database server. The TP monitor accepts the transaction, queues it and manages it till completion. This helps the operating system from being overwhelmed.
References:
http://en.wikipedia.org/wiki/ACID
http://www.peterindia.net/N-tierApplicationsView.html
ACID (atomicity, consistency, isolation, durability) is a set of properties that guarantee that database transactions are processed reliably. This really refers to what can be described of a single logical operation called transaction. For example, in a sql server database, I may choose to update a customer records in two tables. Usually, I would update the record in one table first followed by the next table. But it may result in such that only one table is updated due to some errors. Using transaction, it would mean that either both the table is updated or none is updated. Once the transaction is completed, the database will be in a consistent state and the changes made by the transaction is permanently stored in the database.
2. Describe a TP monitor environment. How can a TP monitor stop an operating system being overwhelmed?
A TP monitor is a control program that manages the transfer of data between multiple local and remote terminals and the application programs that serve them. It provides integrity by making sure that transactions do not get lost. It has the ability to update multiple different databases in a single transaction and has the ability to attach priority to transactions and provide security.
With the TP monitor technology, a client connects to the TP monitor instead of the database server. The TP monitor accepts the transaction, queues it and manages it till completion. This helps the operating system from being overwhelmed.
References:
http://en.wikipedia.org/wiki/ACID
http://www.peterindia.net/N-tierApplicationsView.html
Exercise 10 - Topic 8
1. Find definitions for wigth terms and concepts used in threaded programming:
i. Thread Synchronisation
ii. Locks
iii. Deadlock
iv. Semaphores
v. Mutex (mutual exclusion)
vi. Thread
vii. Event
viii.Waitable timer.
Thread Synchronisation is the mechanism to ensure that two concurrently running threads do not execute specific sections of the program simultaneously.
Locks make sure that no two or more threads can access a particular resource at the same time.
Deadlock is the state no further progress on the program can be made.
A semaphore is a protected variable or abstract data type that constitutes a classic method of controlling access by several processes to a common resource in a parallel programming environment.
Mutual exclusion (mutex) algorithms are used in concurrent programming to avoid the simultaneous use of a common resource, such as a global variable, by pieces of computer code called critical sections.
A thread is the unit of execution within a process.
An event (also called event semaphore) is a type of synchronization mechanism that is used to indicate to waiting processes when a particular condition has become true.
A waitable timer object is a synchronization object whose state is set to signaled when the specified due time arrives.
References:
http://en.wikipedia.org/wiki/Mutex
http://en.wikipedia.org/wiki/Semaphore_(programming)
http://en.wikipedia.org/wiki/Event_%28synchronization_primitive%29
http://msdn.microsoft.com/en-us/library/ms687012(VS.85).aspx
2. A simple demonstration of the threading module in Python (threddemo.py) that uses both a lock and semaphore to control concurrency is by Ted Herman at the University of Iowa. The code and sample output below are worth a loo. Report your findings.
The code is an example of how threads are run in Python. In the code, the numtasks variable is used to determine the max number of tasks. The variable sema is used to create a semaphore which determine how many threads can be run at a time. The mutex variable is used to create a lock.
In the code, the threads are started and the semaphore is acquired. Once acquired, only 3 threads could run at a time. The first 3 threads ran and when each completed, a new thread started executing until all the threads completed to run.
i. Thread Synchronisation
ii. Locks
iii. Deadlock
iv. Semaphores
v. Mutex (mutual exclusion)
vi. Thread
vii. Event
viii.Waitable timer.
Thread Synchronisation is the mechanism to ensure that two concurrently running threads do not execute specific sections of the program simultaneously.
Locks make sure that no two or more threads can access a particular resource at the same time.
Deadlock is the state no further progress on the program can be made.
A semaphore is a protected variable or abstract data type that constitutes a classic method of controlling access by several processes to a common resource in a parallel programming environment.
Mutual exclusion (mutex) algorithms are used in concurrent programming to avoid the simultaneous use of a common resource, such as a global variable, by pieces of computer code called critical sections.
A thread is the unit of execution within a process.
An event (also called event semaphore) is a type of synchronization mechanism that is used to indicate to waiting processes when a particular condition has become true.
A waitable timer object is a synchronization object whose state is set to signaled when the specified due time arrives.
References:
http://en.wikipedia.org/wiki/Mutex
http://en.wikipedia.org/wiki/Semaphore_(programming)
http://en.wikipedia.org/wiki/Event_%28synchronization_primitive%29
http://msdn.microsoft.com/en-us/library/ms687012(VS.85).aspx
2. A simple demonstration of the threading module in Python (threddemo.py) that uses both a lock and semaphore to control concurrency is by Ted Herman at the University of Iowa. The code and sample output below are worth a loo. Report your findings.
The code is an example of how threads are run in Python. In the code, the numtasks variable is used to determine the max number of tasks. The variable sema is used to create a semaphore which determine how many threads can be run at a time. The mutex variable is used to create a lock.
In the code, the threads are started and the semaphore is acquired. Once acquired, only 3 threads could run at a time. The first 3 threads ran and when each completed, a new thread started executing until all the threads completed to run.
Exercise 9 - Topic 7
1. Find out about SET and the use of RSA 128-bit encryption for e-commerce.
The SET ENCRYPTION PASSWORD states that the default password and hint will be used for encryption and decryption. The password is not related to authentication but to the actual encryption and decryption process.
RSA is an algorithm for public key cryptography. It involves public key and a private key. Messages can be encrypted using the public key and can only be decrypted using the private key.
2. What can you find out about network and host-based intrusion detection systems?
Network-based intrusion detection systems use raw network packets as the data source. It monitors and analyzes all traffic in real-time as it travels through the network. It uses the following 4 techniques to recognise an attack.
i. Pattern, expression or bytecode matching,
ii. Frequency or threshold crossing
iii.Correlation of lesser events
iv. Statistical anomaly detection
Host-based intrusion detection systems work best in simple environments. It relies on auditing logs for suspicious activities.
3. What is 'phishing'?
Phishing is the process of attempting to acquire sensitive information like usernames, password, credit card details, etc by pretending to be trustworthy entity in an electronic communication like email.
4. What is SET and how does it compare with SSL as a platform for secure electronic transaction? Is SET in common use?
As described previously, SET is related to the enecryption and decryption process.
SSL is the standard security technology for establishing an encrypted link between a web server and a browser. This ensures all data passed between the client and the server is authenticated. To create a SSL connection, the web server needs to have a SSL certificate. This needs to be obtained from a Certification Authority who validates all the server's details before issuing the certificate. The web server will match the SSL certificate to the private key.
SET is not commonly used. SSL is the industry standard and is widely used.
5. What are cookies and how are they used to improve security? Can the cookies be a security risk?
A cookie is a small text file (less than 4KB) that is sent by the web server and stored in the client's computer. The cookie can contain information that can be later used by the server for client identification. Cookies contain attributes to determine which host names, URI path can access the cookie and may also contain a expiry date.
Cookies give the impression of a session and can be used by the server to check if the client is validated or not. Cookies can also contain access control information after a user is validated. This reduces the server resources by not needing to validate the client each time the request is sent.
However, this also leads to a security issue. For example, an eavesdropper armed with a packet sniffer could simply inercept the cookie as it passes from the browser to the server using it to obtain free access to the site.
That's why, cookies should contain as little private information as possible.
6. What makes a firewall a good security investment? Accessing the internet, find two or three firewall vendors. Do they provide hardware, software or both.
A firewall is a part of computer system or network that is designed to authorize each request to the server. It is a device or a set devices configured to permit or deny requests based on rules and other criteria. This makes it a good investment since it can be used to authorize clients.
Firewalls can be implemented in either hardware or software or both.
7. What measures should e-commerce provide to create trust among their potential customers? What measures can be verified by the customer?
E-commerce websites should be created such that the potential customer is aware that it is secure to pass on credit card details and other personal details and should be made aware of any privacy statements. The following are some other measures that can be verified by the customer.
i. All transactions from the site should be secure - that is, use https and not http.
ii. A session should time-out after a definite time interval. (system)
iii. Customer should be always aware about the amount they are paying.
iv. Customer should have the option to update orders before it is completed.
v. Custome should be made aware where the payment is going and should receive necessary information regarding the purchase.
8. Get the latest PGP information from http://en.wikipedia.org/wiki/Pretty_Good_privacy.
The use of digital certificates and passports are just two examples of many tools for validating legitimate users and avoiding consequences such as identity theft. What others exist?
i. SSL is used to authenticate users on the web.
ii. Firewall is used to authorize users before giving them access to any resource.
iii. Anti-virus programs exist to identify and eliminate viruses and malware.
References:
http://publib.boulder.ibm.com/infocenter/iseries/v5r3/index.jsp?topic=/db2/rbafzmstsetep.htm
http://en.wikipedia.org/wiki/RSA
http://documents.iss.net/whitepapers/nvh_ids.pdf
http://en.wikipedia.org/wiki/Phishing
http://info.ssl.com/article.aspx?id=10241
http://www.w3.org/Security/Faq/wwwsf2.html
http://en.wikipedia.org/wiki/Firewall_%28computing%29
The SET ENCRYPTION PASSWORD states that the default password and hint will be used for encryption and decryption. The password is not related to authentication but to the actual encryption and decryption process.
RSA is an algorithm for public key cryptography. It involves public key and a private key. Messages can be encrypted using the public key and can only be decrypted using the private key.
2. What can you find out about network and host-based intrusion detection systems?
Network-based intrusion detection systems use raw network packets as the data source. It monitors and analyzes all traffic in real-time as it travels through the network. It uses the following 4 techniques to recognise an attack.
i. Pattern, expression or bytecode matching,
ii. Frequency or threshold crossing
iii.Correlation of lesser events
iv. Statistical anomaly detection
Host-based intrusion detection systems work best in simple environments. It relies on auditing logs for suspicious activities.
3. What is 'phishing'?
Phishing is the process of attempting to acquire sensitive information like usernames, password, credit card details, etc by pretending to be trustworthy entity in an electronic communication like email.
4. What is SET and how does it compare with SSL as a platform for secure electronic transaction? Is SET in common use?
As described previously, SET is related to the enecryption and decryption process.
SSL is the standard security technology for establishing an encrypted link between a web server and a browser. This ensures all data passed between the client and the server is authenticated. To create a SSL connection, the web server needs to have a SSL certificate. This needs to be obtained from a Certification Authority who validates all the server's details before issuing the certificate. The web server will match the SSL certificate to the private key.
SET is not commonly used. SSL is the industry standard and is widely used.
5. What are cookies and how are they used to improve security? Can the cookies be a security risk?
A cookie is a small text file (less than 4KB) that is sent by the web server and stored in the client's computer. The cookie can contain information that can be later used by the server for client identification. Cookies contain attributes to determine which host names, URI path can access the cookie and may also contain a expiry date.
Cookies give the impression of a session and can be used by the server to check if the client is validated or not. Cookies can also contain access control information after a user is validated. This reduces the server resources by not needing to validate the client each time the request is sent.
However, this also leads to a security issue. For example, an eavesdropper armed with a packet sniffer could simply inercept the cookie as it passes from the browser to the server using it to obtain free access to the site.
That's why, cookies should contain as little private information as possible.
6. What makes a firewall a good security investment? Accessing the internet, find two or three firewall vendors. Do they provide hardware, software or both.
A firewall is a part of computer system or network that is designed to authorize each request to the server. It is a device or a set devices configured to permit or deny requests based on rules and other criteria. This makes it a good investment since it can be used to authorize clients.
Firewalls can be implemented in either hardware or software or both.
7. What measures should e-commerce provide to create trust among their potential customers? What measures can be verified by the customer?
E-commerce websites should be created such that the potential customer is aware that it is secure to pass on credit card details and other personal details and should be made aware of any privacy statements. The following are some other measures that can be verified by the customer.
i. All transactions from the site should be secure - that is, use https and not http.
ii. A session should time-out after a definite time interval. (system)
iii. Customer should be always aware about the amount they are paying.
iv. Customer should have the option to update orders before it is completed.
v. Custome should be made aware where the payment is going and should receive necessary information regarding the purchase.
8. Get the latest PGP information from http://en.wikipedia.org/wiki/Pretty_Good_privacy.
The use of digital certificates and passports are just two examples of many tools for validating legitimate users and avoiding consequences such as identity theft. What others exist?
i. SSL is used to authenticate users on the web.
ii. Firewall is used to authorize users before giving them access to any resource.
iii. Anti-virus programs exist to identify and eliminate viruses and malware.
References:
http://publib.boulder.ibm.com/infocenter/iseries/v5r3/index.jsp?topic=/db2/rbafzmstsetep.htm
http://en.wikipedia.org/wiki/RSA
http://documents.iss.net/whitepapers/nvh_ids.pdf
http://en.wikipedia.org/wiki/Phishing
http://info.ssl.com/article.aspx?id=10241
http://www.w3.org/Security/Faq/wwwsf2.html
http://en.wikipedia.org/wiki/Firewall_%28computing%29
Exercise 7. Topic 4
1. Why is the perception getting stronger that integration will become a critical factor in coming days?
At present, there is a number application frameworks out there built in a number of programming languages. Many software and web sites are creating services that rely on services created by different software and integrate multiple services from different sources to create new services. This is a challenge for developers to integrate various services together.
One of the ways to face this challenge to create web services and make it available to necessary clients. Data can be passed to the necessary clients via xml.
2. What is the relationship of AJAX to JQuery (jquery.com) and the lightweight Web 2.0 javascript framework called MooTools (mootools.net) within the enterprise software architecture?
JQuery and MooTools are open-source javascript frameworks. MooTools is an extension of JavaScript and improves various JavaScript functions. JQuery on the other hand, focuses on DOM and simplifies traversing HTML documents and handling events. These two frameworks serve different purpose and both offers reusability and provides wrapper classes to work with Ajax simpler.
AJAX - asynchronous JavaScript and XML - is a web development technique to create interactive web applications. Ajax supports partial page updates - that is, retrieves information from the web server without causing the page to reload completely. JavaScript is used to pass the call to the server to retrieve the data from the server. This call is passed and data is retrieved using the XMLHttpRequest object. JQuery provides an ajax api to call methods. MooTools provide wrapper object - Request class - to support Ajax.
3. What are the similarities between the object-oriented development using model-view-controller (MVC) in Ruby on Rails 2.0 and Action Script 2.0 (Flash animations)?
Model view controller is a development framework where teh application is divided into model, view and controller from development perspective. The view, the user interface, is where a user would interact with the application. The interaction would be processed by controller which will either retrieve or update data to the model.
Ruby on Rails uses the MVC architecture pattern to organise application programming. It includes in-built development tasks that can automatically create models and views needed for a basic website.
ActionScript uses an open-source framework - PureMVC - to create MVC applications.
4. What does it mean to develop RESTful practices into our web applications?
RESTful (Representational State Transfer (REST)) is a software architecture designed for World Wide Web. RESTful means to conform to REST constraints.
RESTful architecture consists of clients and servers. Clients send requests to the server and the server returns a response. For a web application to be RESTful, it needs to follow the contraints of REST architecture. The following are the constraints.
i. Client-server: Client and server are separated by a uniform interface. This means that the client is concerned only with user interface and user state while the server is concerned with data storage. This means that the client code can be improved and the server architecture made more scalable.
ii. Stateless: The client-server communication is stateless. That is, the client needs to send all the information necessary to service a request. The state is only stored in the client.
iii. Cacheable: This means that responses from the server must be cacheable. This will improve scalability and performance.
iv. Layered System: A client is not aware if it is connected to the end server or not. Inermediary server can improve system scalability by enabling load-balancing and by providing shared caches.
v. Code on demand (optional): Servers can customize the functionality of a client by transferring logic to that it can execute. JavaScript is an example of this.
vi. Uniform interface: The uniform interface of client-server simplifies the architecture and enables each part to be changed independently.
References:
http://api.jquery.com/jQuery.ajax/
http://mootools.net/
http://en.wikipedia.org/wiki/Model%E2%80%93view%E2%80%93controller
http://en.wikipedia.org/wiki/PureMVC
At present, there is a number application frameworks out there built in a number of programming languages. Many software and web sites are creating services that rely on services created by different software and integrate multiple services from different sources to create new services. This is a challenge for developers to integrate various services together.
One of the ways to face this challenge to create web services and make it available to necessary clients. Data can be passed to the necessary clients via xml.
2. What is the relationship of AJAX to JQuery (jquery.com) and the lightweight Web 2.0 javascript framework called MooTools (mootools.net) within the enterprise software architecture?
JQuery and MooTools are open-source javascript frameworks. MooTools is an extension of JavaScript and improves various JavaScript functions. JQuery on the other hand, focuses on DOM and simplifies traversing HTML documents and handling events. These two frameworks serve different purpose and both offers reusability and provides wrapper classes to work with Ajax simpler.
AJAX - asynchronous JavaScript and XML - is a web development technique to create interactive web applications. Ajax supports partial page updates - that is, retrieves information from the web server without causing the page to reload completely. JavaScript is used to pass the call to the server to retrieve the data from the server. This call is passed and data is retrieved using the XMLHttpRequest object. JQuery provides an ajax api to call methods. MooTools provide wrapper object - Request class - to support Ajax.
3. What are the similarities between the object-oriented development using model-view-controller (MVC) in Ruby on Rails 2.0 and Action Script 2.0 (Flash animations)?
Model view controller is a development framework where teh application is divided into model, view and controller from development perspective. The view, the user interface, is where a user would interact with the application. The interaction would be processed by controller which will either retrieve or update data to the model.
Ruby on Rails uses the MVC architecture pattern to organise application programming. It includes in-built development tasks that can automatically create models and views needed for a basic website.
ActionScript uses an open-source framework - PureMVC - to create MVC applications.
4. What does it mean to develop RESTful practices into our web applications?
RESTful (Representational State Transfer (REST)) is a software architecture designed for World Wide Web. RESTful means to conform to REST constraints.
RESTful architecture consists of clients and servers. Clients send requests to the server and the server returns a response. For a web application to be RESTful, it needs to follow the contraints of REST architecture. The following are the constraints.
i. Client-server: Client and server are separated by a uniform interface. This means that the client is concerned only with user interface and user state while the server is concerned with data storage. This means that the client code can be improved and the server architecture made more scalable.
ii. Stateless: The client-server communication is stateless. That is, the client needs to send all the information necessary to service a request. The state is only stored in the client.
iii. Cacheable: This means that responses from the server must be cacheable. This will improve scalability and performance.
iv. Layered System: A client is not aware if it is connected to the end server or not. Inermediary server can improve system scalability by enabling load-balancing and by providing shared caches.
v. Code on demand (optional): Servers can customize the functionality of a client by transferring logic to that it can execute. JavaScript is an example of this.
vi. Uniform interface: The uniform interface of client-server simplifies the architecture and enables each part to be changed independently.
References:
http://api.jquery.com/jQuery.ajax/
http://mootools.net/
http://en.wikipedia.org/wiki/Model%E2%80%93view%E2%80%93controller
http://en.wikipedia.org/wiki/PureMVC
Tuesday, March 30, 2010
Exercise 6 - Topic 4
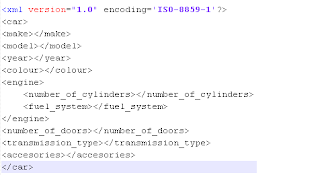
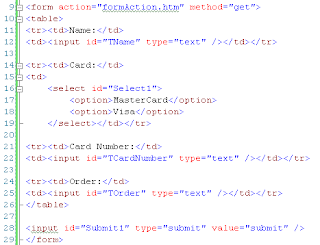
1. Design the form. 'Retrofit' the form data string above:
2. Write the script.
Script archives exist for PERL, Python and JavaScript. Search the web for a script that processes the HTML form data. Read the code and list the steps involved in processing the form.
To use perl to get the form values, the steps are below:
i. Get the query string.
ii. Split the query string by the ampersand symbol "&".
iii. Split the resultant based on "=" symbol to get the key-value pair.
3. Can you modify the script to process the form.
4. Improve the user experience by add a JavaScript feature.
JavaScript can be added to validate forms. However, it cannot br relied upon since users can choose to disable scripts.
name=Evan+Burke&card=Visa&number=8443261344895544&order=French+perfume
for buying some French perfume into the HTML form fields and submit button on the Web page form.
for buying some French perfume into the HTML form fields and submit button on the Web page form.
2. Write the script.
Script archives exist for PERL, Python and JavaScript. Search the web for a script that processes the HTML form data. Read the code and list the steps involved in processing the form.
To use perl to get the form values, the steps are below:
i. Get the query string.
ii. Split the query string by the ampersand symbol "&".
iii. Split the resultant based on "=" symbol to get the key-value pair.
3. Can you modify the script to process the form.
4. Improve the user experience by add a JavaScript feature.
JavaScript can be added to validate forms. However, it cannot br relied upon since users can choose to disable scripts.
Monday, March 29, 2010
Exercise 5
1. Investigate the SQL Server 2008 architecture available from the Dreamspark website.
Microsoft SQL Server 2008 allows organisations to run mission-critical applications, lowers data infrastructure cost and deliver information to all users. It provides robust security features, reliability and scalability for mission-critical applications.
Transparent Data Encryption
SQL Server 2008 enables encryption of entire databases, data files, and log files, without the need for application changes.
External Key Management
SQL Server 2008 provides a comprehensive solution for encryption and key management.
Enhanced Auditing
SQL Server 2008 improves compliance and security by enabling you to audit activity on your data.
Enhanced Database Mirroring
SQL Server 2008 provides a reliable platform for enhanced database mirroring. New features include:
Microsoft SQL Server 2008 allows organisations to run mission-critical applications, lowers data infrastructure cost and deliver information to all users. It provides robust security features, reliability and scalability for mission-critical applications.
Transparent Data Encryption
SQL Server 2008 enables encryption of entire databases, data files, and log files, without the need for application changes.
External Key Management
SQL Server 2008 provides a comprehensive solution for encryption and key management.
Enhanced Auditing
SQL Server 2008 improves compliance and security by enabling you to audit activity on your data.
Enhanced Database Mirroring
SQL Server 2008 provides a reliable platform for enhanced database mirroring. New features include:
- Automatic page repair
- Improved performance
- Enhanced supportability
Resource Governor
Resource Governor enables database administrators to define resource limits and priorities for different workloads
Data Compression
SQL Server 2008 allows efficient storage of data.
Backup Compression:
SQL Server 2008 requires less disk space is required to keep backups online allowing backups to run faster.
Performance Data Collection:
SQL Server 2008 provides new monitoring and reporting tools to allow database administrators to help performance tuning.
Streamlined Installation:
SQL Server 2008 provides improvements in installation, setup and configuration architecture.
T-SQL improvements:
There has been improvements in T-SQL allowing users to pass table name as parameters and new data types like DATE and TIME has been added.
Beyond Relational Data:
SQL Server 2008 allows storage of wide variety of non-relational data types. This includes FileStream data type (large binary files), Geographical Information (geodetic spatial data), Hierarchy ID (system type to stire values that represent nodes in a heirarchy tree).
Resource:
http://download.microsoft.com/download/6/9/d/69d1fea7-5b42-437a-b3ba-a4ad13e34ef6/SQL2008_ProductOverview.docx
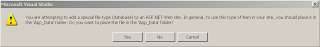
2. Test out SQL Server Express as a lightweight application development tool. SQL Server Express edition and report your findings.
SQL Server Express is a free edition of Microsoft SQL Server but it has some limitations. It can only work on 1 CPU, consume 1 GB Ram max and can have a database size of 4 GB.
The database can be easily created using Visual Studio or by using Microsoft SQL Server Management Studio.
I have setup a database using Visual Studio 2008 as shown below.
At first, right-clicked on the solution explorer and choose to add a new item and selected the database option.
Then, a SQL Server Express database is added to App_Data folder.
The server explorer looks like below.
As can be seen, there are options to add tables, views, stored procedure, etc as can be seen on SQL Server Management Studio.
Then, right clicked on the table, and chose to add a new table.
As can be seen, I have a table assigned various data-types to different fields. Fields like heirarchy id, date are new to SQL Server 2008. There are other interesting data types like xml and image. The xml data type enables to add a whole xml document or chunks of a xml document. The image field allows uploading image files as binary data. Fields can also be set up to have null values.
To set a primary key for the table, select the field, make sure it does not except null, right click on the field and choose "Set primary Key". To set it to an auto-number, go to the Identity-specification section and set "Is Identity" to "Yes".
Saturday, March 13, 2010
Exercise 4 - Topic 2
1. Describe the important and distinguishing properties of Peer to Peer computing with the client/server architecture?
In the client-server network architecture, a central server handles all security and file transactions. In peer-to-peer network architecture, each machine handles shares it's own resources and handles it's own security. Client server architecture is more expensive since it requires the central server and requires special software.
Client server architecture provides administrative tools which is useful where security is important. Network security can be controlled from a central location using the admin tools. Peer to peer architecture requires security to be controlled by end users making it very difficult to implement a secure environment.
2. Frameworks for development. Compare and contrast any TWO of...
Java vs .NET
Java and .NET are both object oriented programming languages. Java was introduced by Sun MicroSystem while .NET was introduced by Microsoft. Both the languages derive it's syntax from C and C++ and both has further improved the language in it's way.
Java's web application framework - J2EE consisting of Jsp, Servlets, JavaBeans runs together making it possible to create a model-view-controller approach to web applications.
.NET's web application framework - asp.net can be written in both C# and VB. This framework contains a lot of controls that are pre-built and can be easily used. This makes it quite easy to use the application. Asp.net allows to create separate layers like (business logic layer, data access layer, presentation layer) to keep the code separate. .NET has recently introduced it's Model View Controller framework for building web applications using the model-view-controller pattern.
Source:
http://technet.microsoft.com/en-us/library/cc751396.aspx
In the client-server network architecture, a central server handles all security and file transactions. In peer-to-peer network architecture, each machine handles shares it's own resources and handles it's own security. Client server architecture is more expensive since it requires the central server and requires special software.
Client server architecture provides administrative tools which is useful where security is important. Network security can be controlled from a central location using the admin tools. Peer to peer architecture requires security to be controlled by end users making it very difficult to implement a secure environment.
2. Frameworks for development. Compare and contrast any TWO of...
Java vs .NET
Java and .NET are both object oriented programming languages. Java was introduced by Sun MicroSystem while .NET was introduced by Microsoft. Both the languages derive it's syntax from C and C++ and both has further improved the language in it's way.
Java's web application framework - J2EE consisting of Jsp, Servlets, JavaBeans runs together making it possible to create a model-view-controller approach to web applications.
.NET's web application framework - asp.net can be written in both C# and VB. This framework contains a lot of controls that are pre-built and can be easily used. This makes it quite easy to use the application. Asp.net allows to create separate layers like (business logic layer, data access layer, presentation layer) to keep the code separate. .NET has recently introduced it's Model View Controller framework for building web applications using the model-view-controller pattern.
Source:
http://technet.microsoft.com/en-us/library/cc751396.aspx
Friday, March 12, 2010
Exercise 3 - Topic 1
1. Explain DNS and DHCP. How does DNS differ from DHCP configuration?
DNS (Domain Name System) is a naming system for computers, services, or any resource connected to the internet or a private network. It contains relevant information related to domain names for each of the components. It works as a translator between the human friendly computer hostnames and IP addresses.
DHCP (Dynamic Host Configuration Protocol) is a computer networking protocol used by hosts to retrieve IP address assignments and configuration information.
2. Why is it important for your online business application to use a static IP address rather than have it dynamically assigned?
A static IP address is required by businesses in order to host web sites, applications on the internet. Without the fixed IP address, the DNS server mapping from hostnames to IP addresses will not work.
3. What role can the following play in business-to-business e-commerce?
a. Virtual Private Network (VPN) or Grid computing services.
VPN is a secure network through which someone can connect to a domain. This can allow users to run application within that particular domain.
Grid computing combines multiple computers to run together as a virtual computer. This virtual computer can then be used to run applications much more faster.
b. Next generation of wireless mesh networks.
The main benefits of the mesh are the following;
- Cheaper and quicker to deploy.
- Mesh nodes can be deployed anywhere there is power.
- Mesh is more fault tolerant than a central wired network.
c. Cloud or Social Cloud applications.
Small businesses can benefit by deploying software to the Cloud (Software as a Service, SaaS). This software can then be accessed by anyone using a web browser. Businesses can benefit by deploying applications to Cloud as it reduces cost for IT infrastructure and maintenance. Businesses do not have to worry about servers, capacity, etc by paying relatively low price to third party hosting the Cloud.
4. If clouding computing is the "black box", then grid computing is a component as the "white box".
Explain what you interpret about this statement.
Applications are hosted somewhere in the Cloud and users/business are not aware of it's location in the server. The user only need to care if the application is accessible or not. In Grid Computing, the business needs to know whether the application is hosted since it needs to configure the server / network and maintain the application.
Source:
http://en.wikipedia.org/wiki/DHCP
http://en.wikipedia.org/wiki/Domain_Name_System
http://features.techworld.com/mobile-wireless/4129/the-benefits-of-80211s-wireless-mesh-nets/
DNS (Domain Name System) is a naming system for computers, services, or any resource connected to the internet or a private network. It contains relevant information related to domain names for each of the components. It works as a translator between the human friendly computer hostnames and IP addresses.
DHCP (Dynamic Host Configuration Protocol) is a computer networking protocol used by hosts to retrieve IP address assignments and configuration information.
2. Why is it important for your online business application to use a static IP address rather than have it dynamically assigned?
A static IP address is required by businesses in order to host web sites, applications on the internet. Without the fixed IP address, the DNS server mapping from hostnames to IP addresses will not work.
3. What role can the following play in business-to-business e-commerce?
a. Virtual Private Network (VPN) or Grid computing services.
VPN is a secure network through which someone can connect to a domain. This can allow users to run application within that particular domain.
Grid computing combines multiple computers to run together as a virtual computer. This virtual computer can then be used to run applications much more faster.
b. Next generation of wireless mesh networks.
The main benefits of the mesh are the following;
- Cheaper and quicker to deploy.
- Mesh nodes can be deployed anywhere there is power.
- Mesh is more fault tolerant than a central wired network.
c. Cloud or Social Cloud applications.
Small businesses can benefit by deploying software to the Cloud (Software as a Service, SaaS). This software can then be accessed by anyone using a web browser. Businesses can benefit by deploying applications to Cloud as it reduces cost for IT infrastructure and maintenance. Businesses do not have to worry about servers, capacity, etc by paying relatively low price to third party hosting the Cloud.
4. If clouding computing is the "black box", then grid computing is a component as the "white box".
Explain what you interpret about this statement.
Applications are hosted somewhere in the Cloud and users/business are not aware of it's location in the server. The user only need to care if the application is accessible or not. In Grid Computing, the business needs to know whether the application is hosted since it needs to configure the server / network and maintain the application.
Source:
http://en.wikipedia.org/wiki/DHCP
http://en.wikipedia.org/wiki/Domain_Name_System
http://features.techworld.com/mobile-wireless/4129/the-benefits-of-80211s-wireless-mesh-nets/
Exercise 2 - Topic 1
Describe the steps imvolved with the Rapid Evolutionary Prototyping Approach as it applies to developing a web application. How is it related to agile development?
The idea behind using the Rapid Evolutionary Prototyping Approach is to develop a robust prototype in a structured manner and constantly refine it.
Therefore, when building a web application with this approach, the idea would be to develop a part of the system based on the requirements. The, this part of the system, the prototype, will be demonstrated to the stakeholders and the site will be improved and further requirements will be built as the development phase continues. According to Rapid Evolutionary Prototyping Approach, the requirements are never completely understood - that is, the developer of the system does not fully understand the requirements. Therefore the developers need to build the prototype and continually refine and improve it to meet the business's expectation.
Agile development is somewhat similar to Rapid Evolutionary Prototyping Approach in that it is iterative. However, it is different from the first in that it tries to deliver a fully functional system from the start and continually refine it based on inputs from the stakeholders.
Source:
http://en.wikipedia.org/wiki/Software_prototyping#Evolutionary_prototyping
http://en.wikipedia.org/wiki/Agile_software_development
The idea behind using the Rapid Evolutionary Prototyping Approach is to develop a robust prototype in a structured manner and constantly refine it.
Therefore, when building a web application with this approach, the idea would be to develop a part of the system based on the requirements. The, this part of the system, the prototype, will be demonstrated to the stakeholders and the site will be improved and further requirements will be built as the development phase continues. According to Rapid Evolutionary Prototyping Approach, the requirements are never completely understood - that is, the developer of the system does not fully understand the requirements. Therefore the developers need to build the prototype and continually refine and improve it to meet the business's expectation.
Agile development is somewhat similar to Rapid Evolutionary Prototyping Approach in that it is iterative. However, it is different from the first in that it tries to deliver a fully functional system from the start and continually refine it based on inputs from the stakeholders.
Source:
http://en.wikipedia.org/wiki/Software_prototyping#Evolutionary_prototyping
http://en.wikipedia.org/wiki/Agile_software_development
Wednesday, March 10, 2010
Exercise 1 - Topic 1
1. Visit http://yahoo.com and http://facebook.com as examples of online communities.
a) What is meant by an online community and how is it important for e-commerce?
a) What is meant by an online community and how is it important for e-commerce?
An online community is a virtual community that exists online whose members enable its existence through taking part in membership rituals (Amy Jo Kim, 2000) - (source- http://en.wikipedia.org/wiki/Online_community). An online community can be an online information source available to public where anyone can post content, comment, flag as inappropriate or / and rate contents (like Wikipedia).
The online community can also be private where users can choose who can view and interact with their content (eg. http://facebook.com).
The online communities are a great tool for e-commerce applications to market themselves since online communities can provide lot of information about a user. For example, in facebook.com there is an application that suggests a user to send gift to a user he is added to on his / her birthday.
b) Is there a common thread and a local community sense in action?
The online community can also be private where users can choose who can view and interact with their content (eg. http://facebook.com).
The online communities are a great tool for e-commerce applications to market themselves since online communities can provide lot of information about a user. For example, in facebook.com there is an application that suggests a user to send gift to a user he is added to on his / her birthday.
b) Is there a common thread and a local community sense in action?
FaceBook is a social networking site that needs users to sign up and add other users before they can share content with. Mostly, the content are personal and are not open to public. This means content on FaceBook is usually not searchable on the search engines. FaceBook offers an open API through which applications and advertisements can be created that can be customised to be user specific. FaceBook offers users to create or join groups through which they can connect to people with similar interests.
On the other hand, yahoo started as a search engine and has slowly developed various tools including emails, chatting software (Yahoo messenger), news site, etc. Yahoo has created local community sites (portal) for various countries. Yahoo makes money by providing advertisements through it's various products.
2. Visit the famous online store front at http;//www.amazon.com
a) Why has it been a successful site? How does the purchase of a book work?
From a website's perspective, Amazon offers clear information on the products they sell. Amazon offers search functionality through which users can search for products and sort by various options (including bestselling, price, date, etc).
To purchase a book, one must find the book, choose quantity and click on "Add to Cart". Then he / she can click "Proceed to checkout" and either log in or create an account before the user can place order. (Various details like name, email and shipping address is collected on the process).
b) Are there any secure transactions not involving money?
Yes, secure transactions are involved in creating accounts, logins.
3. What happens with new models emerging such as price comparison sites?
Price comparison sites are getting common and is going to increase competition between e-commerce and physical stores. The stores need to react quickly and watch over the competitors with the price deals since, otherwise, they could quite easily lose customers to competitors who offer better prices.
Subscribe to:
Posts (Atom)